
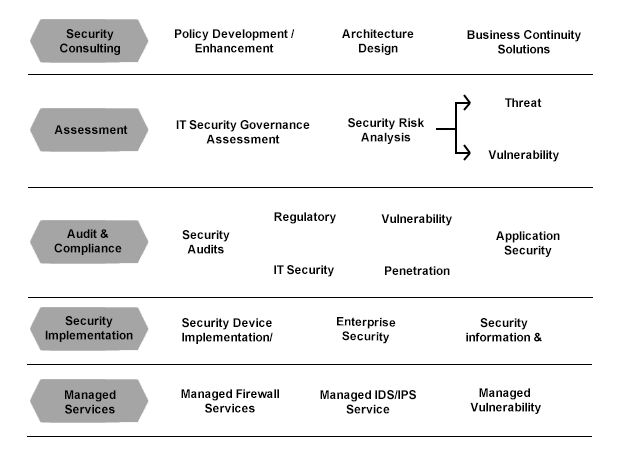
Managed Security Services (MSS)
Organizations often spend a great deal of money on Log Management / Analysis and also on Security Incident & Event Management (SIEM), without satisfactory results. Many organizations struggle with and most SIEM vendors fail to provide effective out of the box correlations. Many organizations continue to expect more of vision fulfillment & process compliance. It is becoming clearer to all that SIEM is not just another tool to be dropped onto the network.
Right Information at the right time, being the backbone of any business, makes it more critical for an organization to protect the information at various levels to ensure the Confidentiality, Integrity and Availability (CIA). This led to IT infrastructure security devices increase, which in turn increases the logs generated by these devices. The monitoring & management of these logs is virtually impossible to be handled manually.
This Leads to:
1. Frequent attacks to critical information infrastructure
2. Address the issue, only after a serious breach
3. Reactive damage control leading to reduction in ability to protect sensitive data forensics and investigation.
We at Dynamic Computer Services, provide a robust platform to provide Managed security services which can be custom built to suit the unique needs of each corporate. The services include:
SIEM (Security Information & Event Management)
a. Log Management and Analysis
- Aggregate data from various security devices including network, security, servers providing ability to consolidate data without any loss of log data.
- Retaining log data based on the compliance adopted
- Advanced data replication and segregation
- Automated Log archival and retrieval
- Automate log classification, normalization, aggregation, and correlation
- Identify anomalies in applications, databases, systems, and devices in real time
- Perform advanced filtered and forensic searches across all logs
- Perform trending analysis across millions of logs in a single view
- Apply advanced data mining techniques for investigations or root cause analysis
b. Log Monitoring and Event Correlation
- 24 x 7 Security Event and Log monitoring and Analysis (Protect against threats)
- Customized escalation procedures
- Automated log analysis and Compliance reporting
- Virtual Integration between security devices and application logs
- Summarized device based compliance reporting enabling easy auditing
- Inbuilt ticket injection engine to track and professionally handle security incidents
c. Alerting and Reporting
Vulnerability Assessment (VA)
- Cataloging assets and capabilities (resources) in a system.
- Assigning quantifiable value (or at least rank order) and importance to those resources
- Identifying the vulnerabilities or potential threats to each resource
- Mitigating or eliminating the most serious vulnerabilities for the most valuable resources
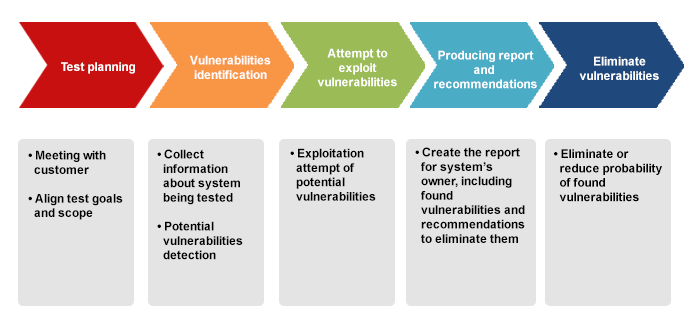
Penetration Testing (PT)
- A penetration test subjects a system or a range of systems to real life security tests. The benefit of a complete penetration suite compared to a normal vulnerability scan system is to reach beyond a vulnerability scan test and discover different weaknesses and perform a much more detailed analysis.
- When performing a penetration test, you have the advantage of a wide range of integrated advanced utilities to do penetration testing. This includes extensive vulnerability scanning, launching of real exploits, buffer overflow attacks, a wide range of advanced utilities and Denial of Service.
Cyber Security Audit
- Data Classification and Mapping, Inventory and Risk Analysis
- Policies, Procedures, Standards and Documentation Review
- Understanding the threats to the organization
- Achieving compliance with international standards
- Internet Perimeter Assessment
- Developing the Security roadmap for the Organization
- Physical Security Audit
The content displayed on this website is sourced from the publicly available information on the websites of our principals, and is displayed here purely for informational purposes to promote our principals' products and services. All terms and conditions applicable to the content on our principals' websites remain applicable to the content displayed on the pages of www.dynamicgroup.in
Call us at +91 9025 66 55 66 to know more about our Software, Hardware & Service offerings!





