The world's largest cloud-based security as a service
Benefit from the cloud intelligence gathered from over 30 billion requests per day.
Your business computing environment has changed completely in the last ten years
Is the way you secure your business computing environment still the same?
Many businesses are still stitching together point products in an attempt to deliver holistic security, despite the huge changes wrought by mobility, Web 2.0, and cloud-based apps. Zscaler's multi-tenant cloud-based architecture, built on a foundation of almost 50 patented technologies, enables the Zscaler security as a service, which is unlike anything else available today.
 Create and push policies globally in near real time — changes are just as easy to do and fast to provision.
Create and push policies globally in near real time — changes are just as easy to do and fast to provision.
 Get worldwide visibility — instantly. Go from at-a-glance dashboard views to the user/device level as fast as you can click.
Get worldwide visibility — instantly. Go from at-a-glance dashboard views to the user/device level as fast as you can click.
 See the whole picture with our integrated platform, instead of just the pixels.
See the whole picture with our integrated platform, instead of just the pixels.
 Benefit from a global footprint; the first time a new threat is blocked for any user, it's blocked for all users.
Benefit from a global footprint; the first time a new threat is blocked for any user, it's blocked for all users.
Secure, policy-based access to any cloud or Internet application from anywhere, on any device
No hardware, no software, no headaches.
Zscaler puts your security policies in context
Most security products will tell you that they provide context awareness, but the fact is true context depends on perspective.
Point products can only offer policy — and visibility — from the perspective of their specialty. It's up to you, and maybe your SIEM, to assemble the mosaic, making real-time visibility impossible. Point products are also limited by the perspective of their location, so when users move, overarching policy may change.
Zscaler's security-as-a-service platform gives you the perspective you need. Because Zscaler is located in the cloud, in over 100 data centers around the world, location is no longer an issue. Zscaler policy can follow your users anywhere, because we are effectively everywhere. And because Zscaler is a complete security platform, not a point product, you can finally create granular, nuanced policies that incorporate many different perspectives.
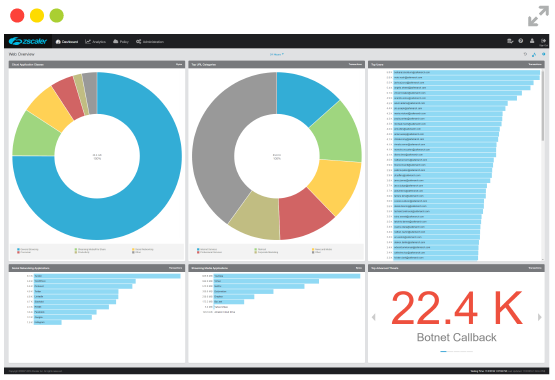
Granular visibility from anywhere, at any time, with Zscaler's global real-time analytics
Your CEO is calling from a remote site to report that his device is acting strangely when connected to the web. Is it an advertiser, or is his device infected? This is a recurring nightmare in the security world. You have to amass information from each of your point products and correlate the results before you can answer the question. And if you're under attack, that's time that you don't have.
With the Zscaler SaaS platform, you just bring up the admin UI and the answer is right there — global, and in real time. You can drill down to the location and user level in just a few clicks. Then you can zoom up and check what is happening with devices around the world, so if you see a threat you can stop it in its tracks.
Outsmart advanced threats with cloud intelligence

Sophisticated attacks don't hit your network head-on in one place. Hackers use changes like user mobility and cloud-based business/personal applications to their advantage. They use a combination of methods, often in tandem, to get past your defenses — because hackers know that advanced persistent threats are difficult to spot with any single security device.
That's why, with Zscaler, every byte of traffic is examined by eight different security engines in real time, allowing you to quickly discover coordinated attacks and block them before they get into your network. But because the Zscaler SaaS platform is built on a global, multi-tenant architecture, we deliver another unique benefit. By virtue of being 100 percent cloud-based, we process more than 30 billion requests a day. And if a threat is discovered for any one of our millions of users, it is blocked for all of our millions of users.
SSL inspection that you can actually use
The current move to SSL — slated to double in North America next year — is posing an enormous issue for security professionals. Obviously you can't be blind to 60% of Internet traffic. But inspecting encrypted content places a huge load on your network, and creates an often unacceptable experience for your users.
Because Zscaler was built to handle encrypted traffic at a global cloud scale, the issue of SSL becomes a non-issue. Zscaler inspects every byte of traffic in real time, including encrypted traffic. So threats have nowhere to hide.

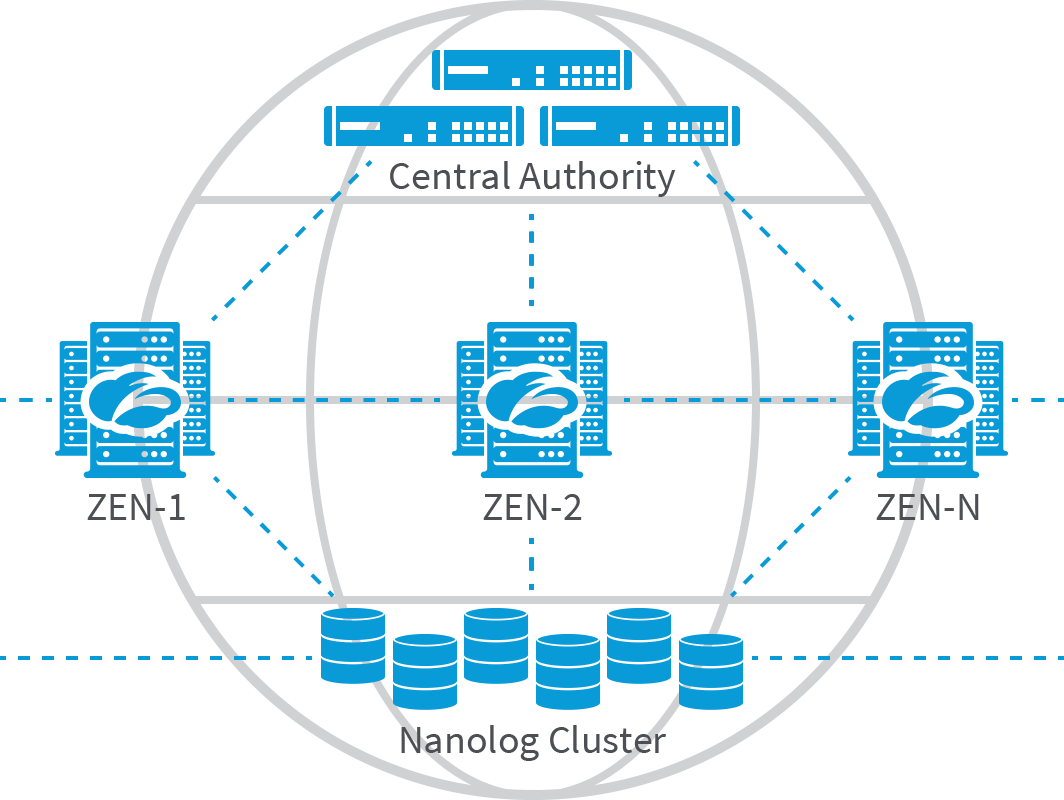
How Zscaler works
Zscaler's architecture was created from scratch as a pure cloud provider. We deliver a truly multi-tenant and highly scalable platform by functionally distributing components of a standard proxy to create a giant global network that acts as a single virtual proxy. Any user can go to any gateway at any time for policy-based secure Internet access. Zscaler infrastructure comprises three key components: Zscaler Enforcement Nodes (ZENs), Central Authority (CA), and Nanolog Servers.
The content displayed on this website is sourced from the publicly available information on the websites of our principals, and is displayed here purely for informational purposes to promote our principals' products and services. All terms and conditions applicable to the content on our principals' websites remain applicable to the content displayed on the pages of www.dynamicgroup.in
Call us at +91 9025 66 55 66 to know more about our Software, Hardware & Service offerings!






