Intercept X for Server
Unmatched Server Protection
Powerful, Server-Specific Protection
Protect the critical applications and data at the core of your organization, whether that data is on physical servers, virtual servers, or in the cloud. Intercept X for Server employs a comprehensive defense-in-depth approach including these essential protections:
Deep Learning Neural Network
Protects against never-before-seen malware
Our constantly updated artificial intelligence model that is trained to look for suspicious attributes of potentially malicious code
Anti-Exploit
Protects against browser, plugin, or Java-based exploit kits even if your servers are not fully patched
Protects against browser, plugin, or Java-based exploit kits even if your servers are not fully patched
Root Cause Analysis
Incident response with forensic detail
Provides the who, what, when, where, and how of a given attack, allowing IT the ability to constantly improve upon their security posture
CryptoGuard and WipeGuard
Stops ransomware and master boot record attacks
Automatically identifies and stops unwanted encryption attempts as well as system-crippling MBR attacks
Anti-Hacker Capabilities
Protects against the most persistent hacking attempts
Prevents pervasive, real-time hacking techniques such as credential harvesting, lateral movement, and code-caving
Server Lockdow
Provides application whitelisting with a single click
Reduces the attack surface by ensuring that only known and trusted application executables can be configured and run on a server
File Integrity Monitoring
Protect critical system files and data
Continuously monitors and tracks unplanned and unexpected changes, to help identify potential PCI DSS security breaches
Cloud Workload Discovery
Find unprotected resources in public cloud
Gain visibility of server workloads running in AWS or Azure, to enforce a consistent security policy
Intercept X for Server Overview
Intercept X for Server leverages cutting-edge protection, including deep learning malware detection, exploit prevention, and technologies designed to stop ransomware and boot record attacks. Unique to Intercept X for Server, the Server Lockdown and Cloud Workload Discovery features ensure that server configurations are safe no matter where they are located.

Stop Exploits and Persistent, Real-Time Hacks
Exploit attacks within server environments can be devastating and are often undetectable by traditional server protection technologies. Intercept X for Server is designed to stop even the most stubborn hackers from leveraging exploit techniques which target credential harvesting, remaining hidden and persistent, or those designed to move laterally across the network between systems and applications.
CryptoGuard Stops Ransomware
CryptoGuard protects servers by stopping the malicious encryption of data and rolling back any changes to a known and safe state. And with Root Cause Analysis, threat discovery and remediation is simple to understand and helps reduce incident response times exponentially.
Discover and Ensure AWS and Azure Workloads are Protected and Compliant
Gain visibility of server workloads running in Amazon AWS or Microsoft Azure and enforce a consistent security policy across both on-premises and cloud environments.

Synchronized Security
Synchronized Security is a best of breed security system that enables your defenses to be as coordinated as the attacks they protect against. It combines an intuitive security platform with award-winning products that actively work together to block advanced threats to give you unparalleled protection
- Shares real-time threat intelligence between servers, endpoints and firewalls
- Protects end users from accessing potentially compromised servers and cloud-hosted applications
- Create simple, actionable insights and automatic resolutions across synchronized products
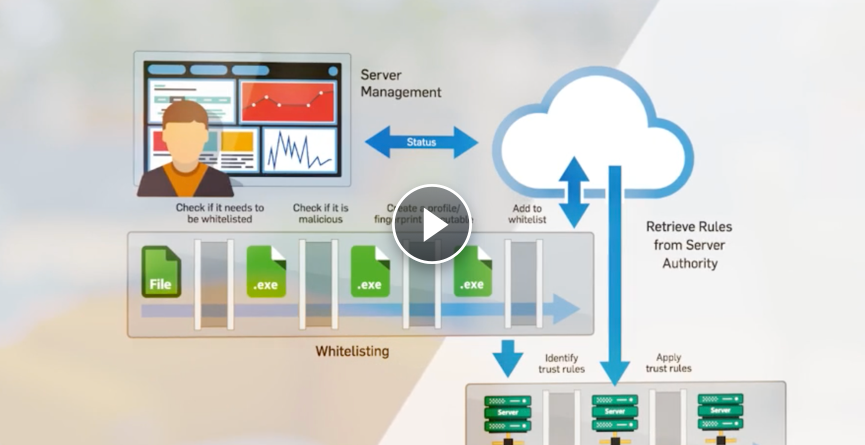
One-Click Server Lockdown
Get powerful change and control management capabilities by whitelisting approved applications and preventing unauthorized server configuration
- Whitelist trusted applications with a single click and block unapproved server changes
- Automatically add exclusions for common server applications to save administrators setup time and help to reduce false positives
- Automatically manage trusted vendor updates and re-register the application in the whitelist
The content displayed on this website is sourced from the publicly available information on the websites of our principals, and is displayed here purely for informational purposes to promote our principals' products and services. All terms and conditions applicable to the content on our principals' websites remain applicable to the content displayed on the pages of www.dynamicgroup.in
Call us at +91 9025 66 55 66 to know more about our Software, Hardware & Service offerings!







